-
Notifications
You must be signed in to change notification settings - Fork 60
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Origin trial token inside iFrames #38
Comments
|
That's puzzling. Would you be able to paste a screenshot of DevTools origin trial information for the page or pages where you're experiencing this? If you can share a link to the page(s), that would be great, but no worries if you can't. I'll check about
Good idea -- I'll add that to developer.chrome.com/docs/web-platform/origin-trials or developer.chrome.com/docs/web-platform/origin-trial-troubleshooting. (@maudnals is out-of-office this week.) |
|
Hi @samdutton , Here is a screenshot of the specific token issue. Please tell me if you were expecting something else. |
|
Thanks @alois-bissuel — I'll take a look. Just to confirm: |
|
Hi @samdutton |
|
Hi there @alois-bissuel. I'm am a member of the Origin Trials support team taking a look at this issue, but I would need some minimal test case to reproduce the problem in order to debug further. Would it be possible to provide this? |
|
Hello @DanielRyanSmith . |
|
I tried this method for some time with no luck reproducing 😔 I'm not sure what causes the loss of secure context here either. Any definitive way to reproduce this would be of great help. Sorry about this issue, but thank you for your thorough descriptions and assistance in investigation. |
|
Hi @DanielRyanSmith (i'm working with @alois-bissuel on this), Here's an example taken from https://www.lachainemeteo.com/meteo-france/previsions-meteo-france-aujourdhui The main google ads iframe is deemed "secure" It wraps another intermediary iframe (not owned by us) which chrome defined as insecure context, even though the url is https://s.hubvisor.io/wrapper/01BYK28ENND8X5G8K0AJ2DPK9E/sandbox.html?pid=ban-atf : which seems to disable the attribution-reporting feature altogether. Our code, making use of the attribution api, is running in a child iframe, but to no avail since the feature is disabled by inheritance. The puzzling question is why the context becomes suddenly insecure in the hierarchy ? is is related to the initialization of this intermediary iframe ? |
|
Hi all, it seems we're looking at an overlapping, if not identical issue in #40 filed by @alois-bissuel. @DanielRyanSmith and all, feel free to chime in - Thanks! |
|
Thanks a lot for the demo @maudnals! I am seeing what is being described in your comment using your demo. I'm still unsure of the cause unfortunately, but I'll update here if I have any additional info. |
|
Hi @alois-bissuel @fabienbk |
|
Could it be that this frame's (In case of redirects, what DevTools displays is the final destination, so if the original src is HTTP we wouldn't see it here Additionally, beyond the secure context aspect:
|
|
Thanks for looking into this @maudnals Regarding your last point, I will check the iFrame src origin, but I guess it is a secure one. I will try to see if there are any hints of redirect in the network tab (please enlighten me if there are other place I can check to be sure of this). |
|
Hello @maudnals, I have looked at the issue again, and I haven't been able to find any definitive proof that a redirect happens or not for the creation of these iFrames. The only hint is that the "topmost" hubvisor iFrame in devtool (Application tab) has a button close to the URL to get the associated network request, and this request has an http code 304. This is a form of redirect to a cached resource if I am not mistaken. I do not know whether this might cause an issue or not, and I have no idea how to reproduce this in a controlled manner. |
|
Closing, as this might be covered in #52. |

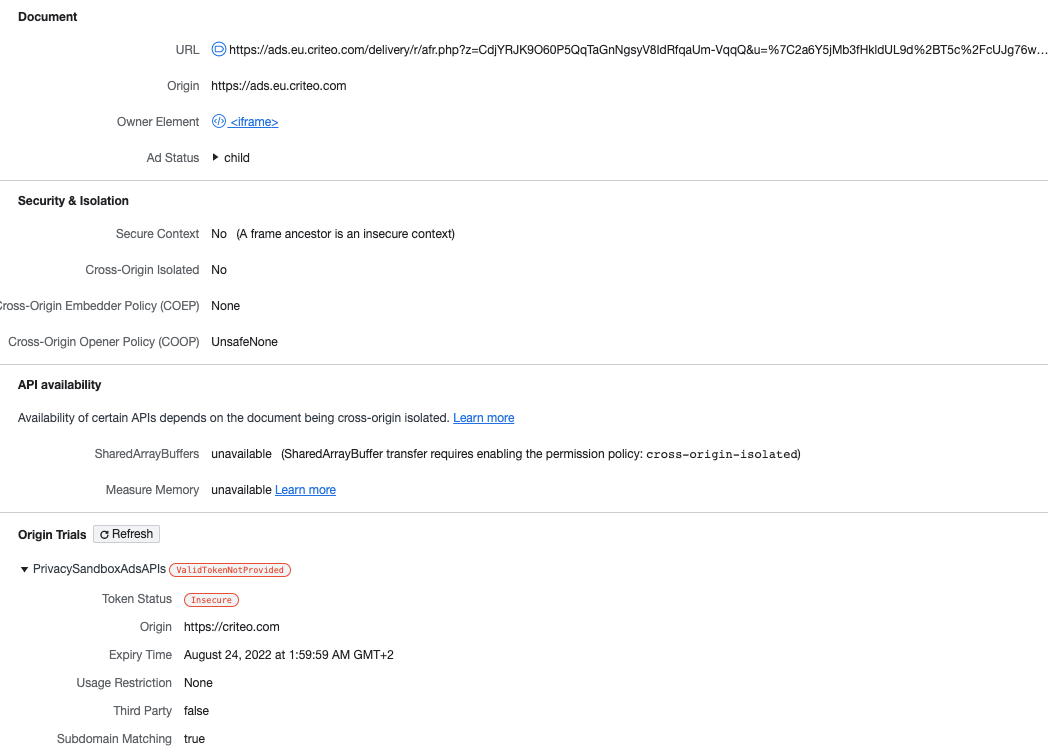
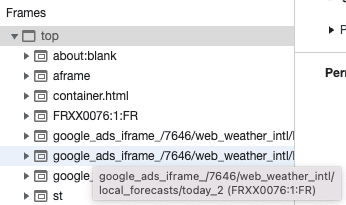




Hello,
We have an issue with OT tokens for the attribution reporting API.
In some cases, our token is declared invalid, its status being "Insecure". I have not been able to find a documentation with all token status and their causes, but I surmise that it comes from our ad being displayed in an insecure iFrame, ie Secure context : No (A frame ancestor is an insecure context).
In our example, all parent iFrames are sourced from https URL.
The only "trail" that we have is that the top iFrame (a Google ads one) uses a srcdoc attribute, instead of a regular src one.
Let me know if you need some further details.
Thanks a lot for your help!
The text was updated successfully, but these errors were encountered: