
That one artifact: How evidence can hide in Apple Note artifacts
In this series, Chad Gish, CID/SISU Detective, Metropolitan Nashville Police Department shares some noteworthy cases in his extensive career where pivotal artifacts, and tools like Magnet Axiom, were able to help close a difficult case.
Being a digital forensic investigator isn’t easy. Long days of inspecting some of the worst material humanity creates, searching for clues; carving through petabytes of pointless information to find the one piece of evidence crucial to solving a case. But the satisfaction of using digital evidence to deliver justice makes it all worthwhile.
Each investigation presents unique circumstances and the artifact that proved pivotal in a previous case have nothing to do with the current one. Usually we’re bringing together a diverse collection of artifacts for a case, but sometimes just a single artifact transforms an investigation from cold to conviction.
In this real scenario, we share how an unusual artifact, an Apple Note, broke a murder investigation open and how Magnet Forensics tools were vital to the process.
An iPhone at the heart of a murder investigation
In a recent murder investigation, the homicide team identified a suspect and conducted interviews, yet evidence remained scarce. Fortunately, probable cause justified the seizure and examination of the suspect’s cell phone.
Despite the iPhone being secured with a six-digit PIN, it was in the After First Unlock (AFU) state, and the digital investigator promptly performed an AFU extraction with Magnet Graykey to acquire a full file system extraction. Magnet Axiom was immediately put through its paces.
The digital forensic investigator received comprehensive briefings on all facets of the investigation, reviewed investigative reports, and engaged in extensive discussions with the homicide investigators to gain a deep understanding of the case. This thorough approach is crucial in the initial phase of an examination to deliver strong analysis from the digital forensics lab.
The detective carefully analyzed data from the suspect’s iPhone. He meticulously reviewed data in various artifact categories where evidence is typically found, including Media, Communication, Web Related, Cloud Storage, Application Usage, and Location and Travel. However, his investigation yielded no significant findings. Equipped with a solid understanding of the crime and case details, he returned the next morning with a fresh strategy: to systematically scrutinize each data category. To his surprise, not only did he recover the smoking gun, it was still warm!
“Lyrics” pointing the way
One of the primary categories he examined that morning was Documents, more specifically, Apple Notes. Among the recovered Apple Notes, one stood out: a note created merely two days after the murder, simply labeled “Lyrics.” Upon inspecting this artifact, it became immediately apparent that the suspect was intricately linked to the murder.
The note contained song lyrics detailing the potential motive behind the murder: a dispute over narcotic sales. Moreover, the lyrics divulged crucial details not disclosed to the public: the make and caliber of the murder weapon, the amount of money stolen, the street name where the crime occurred, the make and model of the getaway vehicle, the number of shots fired, and even the area of the victim’s body that was wounded.
Amid such a tragic crime, an Apple Notes artifact emerged as an unexpected hero.
A category worth a closer look
Apple Notes, despite not always containing evidence, is a data category worthy of examination, as demonstrated by the compelling evidence in the case mentioned above. Apple Notes can contain more than just plain text; users can embed various types of data including audio, images, videos, URLs, and locations directly within them.
Numerous investigations have been solved or significantly aided by evidence found within Apple Notes: from a murder suspect storing getaway plans to a child predator placing email addresses for other CSAM traders, and even to another suspect creating encrypted Apple Notes to record fraudulent bank account numbers. The versatility and potential richness of information within Apple Notes make them an essential element in digital forensic investigations.
Each digital analysis presents its unique challenges and opportunities. While some evidence may be readily apparent and easily accessible—the low-hanging fruit—other crucial pieces of information might be more concealed and require deeper investigation. The key lies in knowing where and how to search effectively, leveraging both established techniques and creative approaches to uncover the evidence needed to solve the case.
How to locate and examine Apple Notes in Axiom

Axiom Examine categorizes Apple Notes and Apple Voice Notes within the Documents category during the digital processing. This categorization allows investigators to efficiently review the content stored within Apple Notes, including text-based notes as well as those containing voice recordings.

As observed in Axiom Examine’s Column View, the ‘Encrypted’ column serves to indicate instances where encryption has been applied to an Apple Note. This feature allows investigators to swiftly identify notes that have been encrypted, potentially signifying the presence of sensitive or protected information.
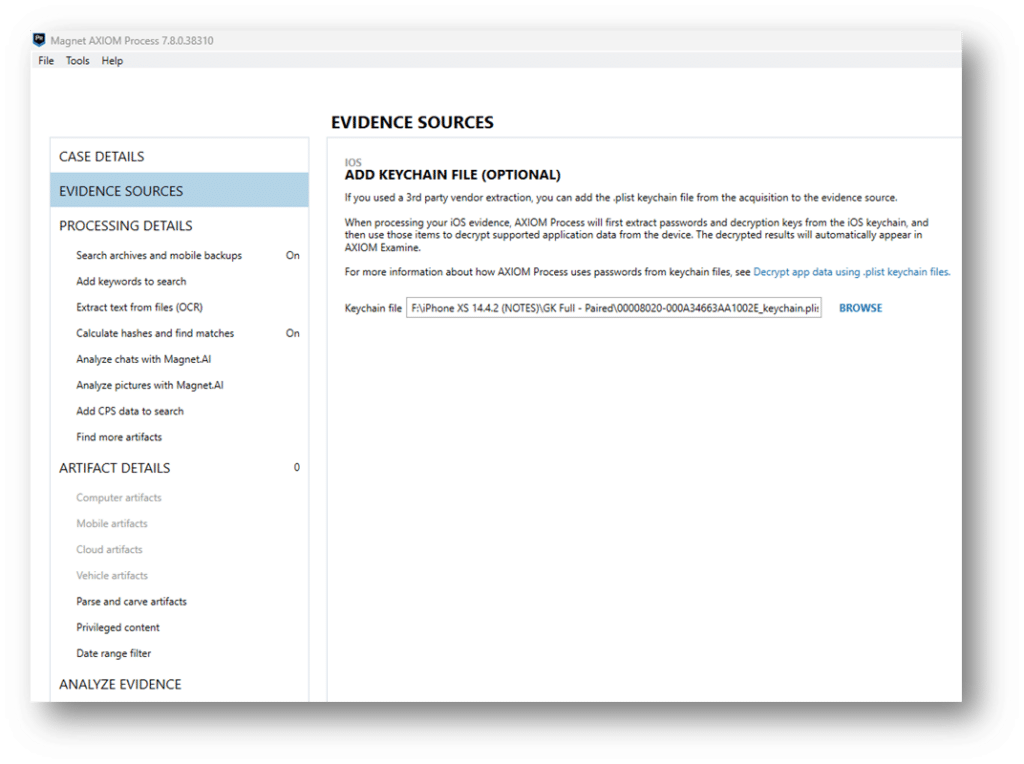
Axiom Process provides support for various encrypted artifacts, with Apple Notes being one of them. In the case of an encrypted Apple Note, a distinct password is utilized, separate from the PIN or Passcode of the device itself, and the password is stored within the iOS Keychain file. During the data extraction process of an iPhone using Magnet Graykey, it is also possible to obtain the keychain file.
As illustrated in the provided exhibit, when loading an iOS image into Axiom Process, there is an option to furnish the keychain file. By doing so, Axiom Process conducts the decryption process utilizing the decryption keys obtained from the iOS Keychain file. This facilitates the retrieval of data from encrypted artifacts, such as Apple Notes, thereby enhancing the efficiency and comprehensiveness of the digital forensic analysis.

Alternatively, if the Apple Notes password(s) are known they can be entered when adding the case to Axiom Process. In the Mobile Artifacts section simply select “Options” and the above dialog box appears.
See for yourself how Magnet Axiom can help
Examine digital evidence from mobile, cloud, computer, and vehicle sources, alongside third-party extractions all in one case file with Magnet Axiom. Learn more about how you can use powerful and intuitive analytical tools to automatically surface case-relevant evidence quickly and try it today.
