Poll Vaulting: Cyber Threats to Global Elections
Mandiant
Written by: Kelli Vanderlee, Jamie Collier
Executive Summary
-
The election cybersecurity landscape globally is characterized by a diversity of targets, tactics, and threats. Elections attract threat activity from a variety of threat actors including: state-sponsored actors, cyber criminals, hacktivists, insiders, and information operations as-a-service entities. Mandiant assesses with high confidence that state-sponsored actors pose the most serious cybersecurity risk to elections.
-
Operations targeting election-related infrastructure can combine cyber intrusion activity, disruptive and destructive capabilities, and information operations, which include elements of public-facing advertisement and amplification of threat activity claims. Successful targeting does not automatically translate to high impact. Many threat actors have struggled to influence or achieve significant effects, despite their best efforts.
-
When we look across the globe we find that the attack surface of an election involves a wide variety of entities beyond voting machines and voter registries. In fact, our observations of past cycles indicate that cyber operations target the major players involved in campaigning, political parties, news and social media more frequently than actual election infrastructure.
-
Securing elections requires a comprehensive understanding of many types of threats and tactics, from distributed denial of service (DDoS) to data theft to deepfakes, that are likely to impact elections in 2024. It is vital to understand the variety of relevant threat vectors and how they relate, and to ensure mitigation strategies are in place to address the full scope of potential activity.
-
Election organizations should consider steps to harden infrastructure against common attacks, and utilize account security tools such as Google’s Advanced Protection Program to protect high-risk accounts.
Introduction
The 2024 global election cybersecurity landscape is characterized by a diversity of targets, tactics, and threats. An expansive ecosystem of systems, administrators, campaign infrastructure, and public communications venues must be secured against a diverse array of operators and methods. Any election cybersecurity strategy should begin with a survey of the threat landscape to build a more proactive and tailored security posture.
The cybersecurity community must keep pace as more than two billion voters are expected to head to the polls in 2024. With elections in more than an estimated 50 countries, there is an opportunity to dynamically track how threats to democracy evolve. Understanding how threats are targeting one country will enable us to better anticipate and prepare for upcoming elections globally. At the same time, we must also appreciate the unique context of different countries. Election threats to South Africa, India, and the United States will inevitably differ in some regard. In either case, there is an opportunity for us to prepare with the advantage of intelligence.
The variety of threat actors and intentions exposes election-related targets to a range of cyber threat vectors. In addition to tactics that Mandiant commonly associates with cyber intrusion activity, such as phishing, exploitation of internet-exposed systems, and data theft, election cyber threat activity also seeks to influence public perceptions and voter choices. The tactics to accomplish this public-facing objective often leverage disruptive tactics. This includes web defacements, DDoS attacks, as well as publicizing intrusions and stolen data via leak sites or social media campaigns. Foreign state aligned information operations disseminate content on websites and social media. This is often intended to mislead target populations or encourage social divisions and mistrust in leaders and institutions.
Despite the variety of cybersecurity challenges facing election ecosystems, it is important for the security community to remain level-headed. Information operations and disruptive cyber campaigns thrive when their impacts are built up. This makes objective and data-driven analysis essential. The variety of election cyber threat vectors presents complexity, but also highlights that direct election result interference attempts account for a small proportion of the overall threat landscape.
Diversity of Targets: Protecting the Entire Election Ecosystem
The attack surface of an election involves a range of entities. This includes election systems and infrastructure, election administrators, entities involved in running the election, and organizations involved in political campaigning — including news and media organizations (Figure 1). The ease of targeting and nature of cyber threat activity (cyber espionage, information operations, extortion, etc.) can vary across entities within these categories.
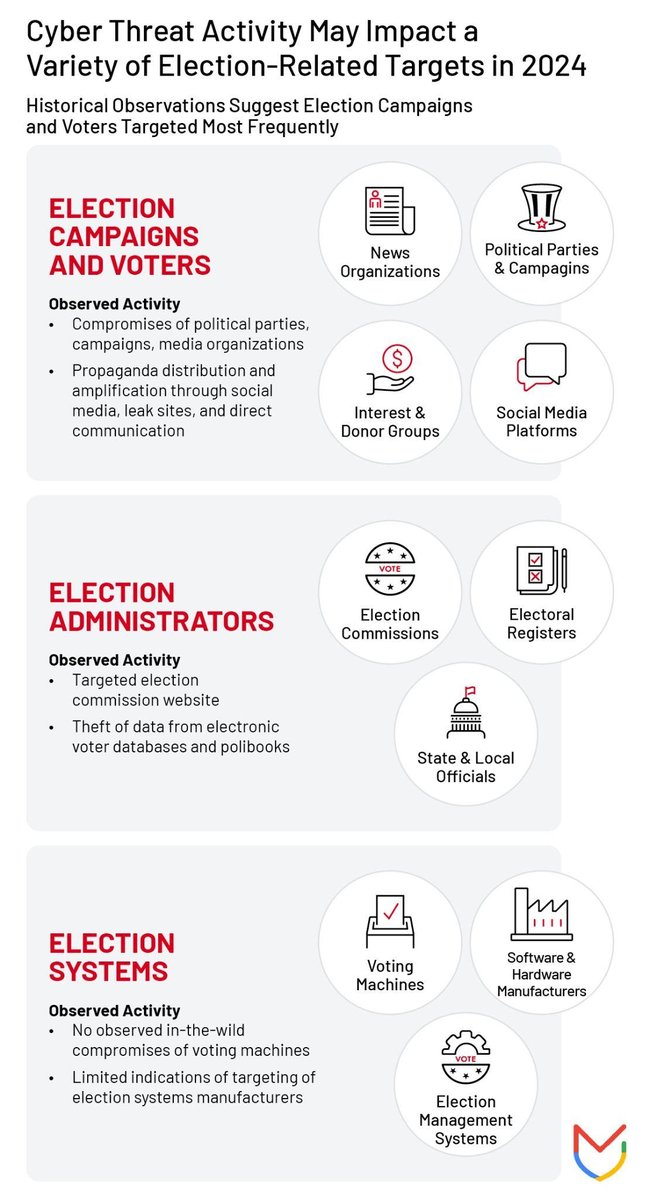

Figure 1: Cyber Threat Activity May Impact a Variety of Election-Related Targets in 2024; Historical Observations Suggest Election Campaigns and Voters Targeted Most Frequently
Diversity of Tactics: Multiple Threat Vectors at Play
With multiple cyber threat vectors impacting election-related infrastructure, it is vital for defenders to identify the most likely scenarios that could impact them.
Figure 2 depicts our best assessment of the relative likelihood and magnitude of a particular cyber threat tactic being used against the three categories of election-related targets described in Figure 1. The likelihood assessments are based on how frequently we have observed or inferred use of these tactics during past election cycles. Magnitude assessments reflect the average amount of time and effort we estimate organizations expend to recover from events using these tactics as well as the strength of official responses to past incidents.
These assessments consider each tactic in isolation. However, Mandiant suggests that the combination of several tactics in the context of a single event would likely increase the severity of the campaign because we have seen this pattern play out during the most serious cyber threat events targeting elections over the last decade. Hack and leak represents a long-standing example of this in action: sensitive information stolen through a network intrusion boosts the effectiveness of subsequent information operations that can leverage authentic documents to maximize societal disruption.
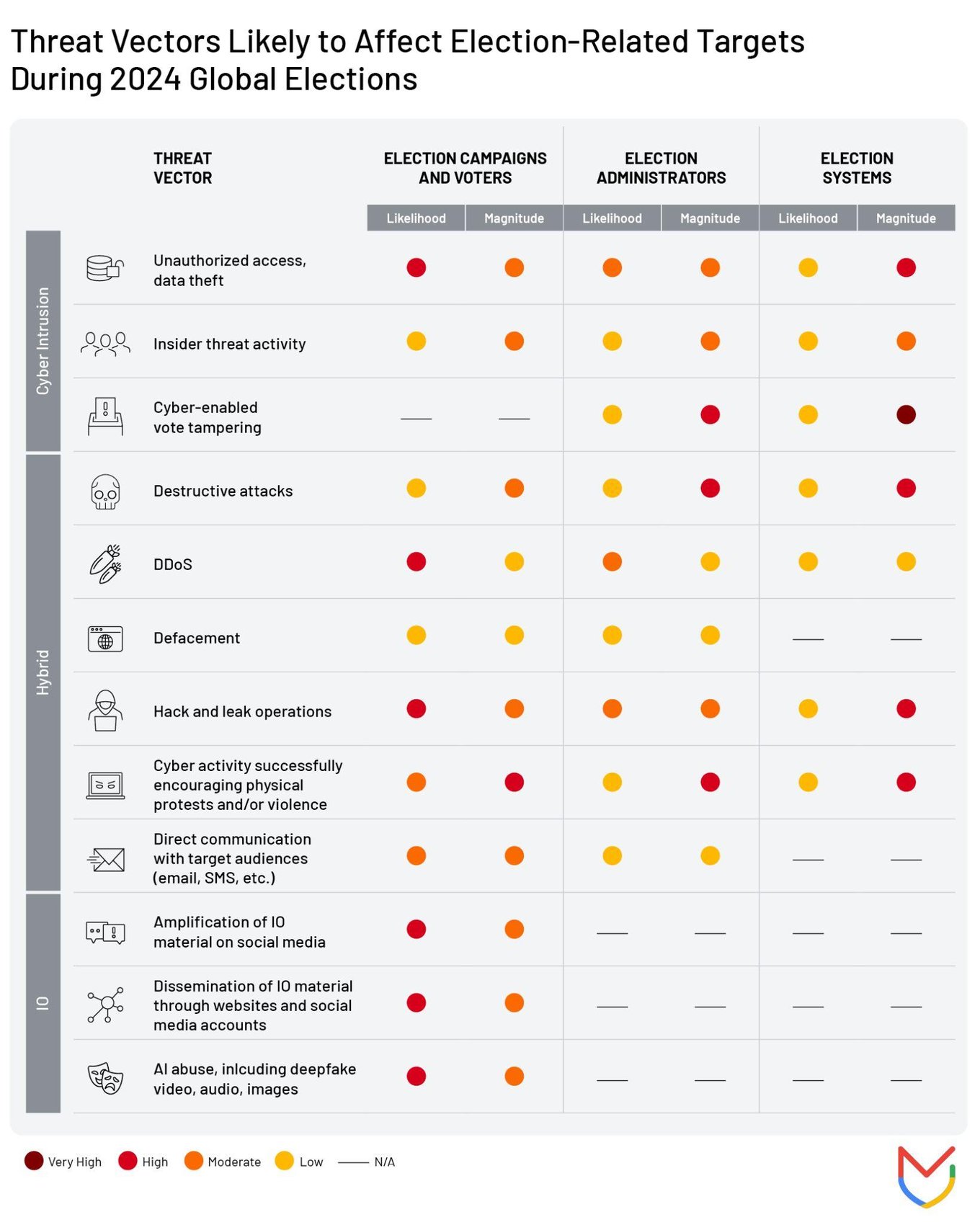

Figure 2: Relevant TTPs for 2024 Global Election-Related Targets
In the most significant cyber incidents targeting elections that Mandiant has tracked, threat actors have deliberately layered multiple tactics in hybrid operations in such a way that the effect of each component magnifies the others.
During the May 2014 Ukrainian presidential election, purported pro-Russian hacktivists CyberBerkut claimed credit for a series of malicious activities against the Ukrainian Central Election Commission (CEC) including a system compromise, destruction of vital data and systems including vote tabulation software, a data leak, a DDoS attack, and an attempted defacement of the CEC website with fake election results. Ukrainian officials suspect that the operation was not conducted by independent hacktivists, citing the presence of malware on affected systems that is confidently attributed to Russian state attributed cyber espionage operators.

Figure 3: Operations Likely to Combine Traditional Cyber Intrusion and IO Tactics
In 2020, Iranian actors attempted to compromise multiple U.S. state voter registration or information websites. They used stolen voter contact information to send threatening emails and social media direct messages impersonating the “Proud Boys” to intimidate U.S. officials and voters.The operation used a video — also featuring stolen voter data — to publicize a false claim of weaknesses in U.S. election systems (Figure 4). On election day, the actors allegedly attempted to log in to a previously compromised media outlet, likely to use the access to disseminate additional false information. U.S. authorities linked the threat actors to Iranian company Emennet Pasargad, which has contracted with the Iranian government.
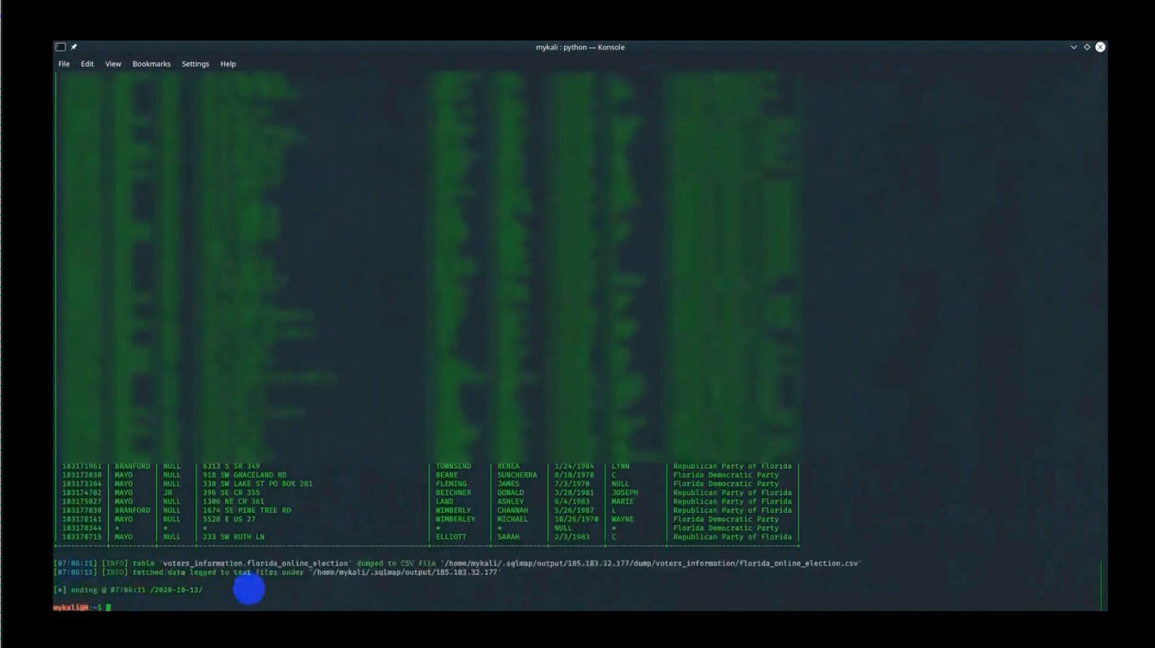

Figure 4: Screenshot from threat actor video
Mandiant has observed similar dynamics of hybrid operations demonstrated frequently during the ongoing Russia-Ukraine conflict.
For example, DDoS attacks disrupted the websites and some online services of Ukrainian government agencies and financial services organizations shortly before the advancement of Russian troops in February 2022. U.S. and UK officials attributed these DDoS attacks to the Russian Main Intelligence Directorate (GRU). On the same day, Ukrainians also received SMS messages claiming that ATM services were malfunctioning, which were debunked by Ukrainian cyber police as inaccurate. While the DDoS attacks only caused short-term technical disruption to online banking services, the overarching aim of the campaign was to undermine public trust in the integrity of the Ukrainian financial services industry and provoke panic in the run-up to a physical conflict.
In fact, the blending of cyber and information operations is an essential pillar of Russia’s strategy. This is reflected in its information confrontation doctrine that combines reconnaissance, disruptive technical effects, and psychological operations (Figure 5). This approach plays out in the wiper operations conducted by the GRU in Ukraine. Here, Russian threat actors steal data from targeted systems, deploy wiper malware, and then telegraph the success of their operations by calling attention to the disruption and providing evidence of a compromise with the stolen materials via Telegram channels.
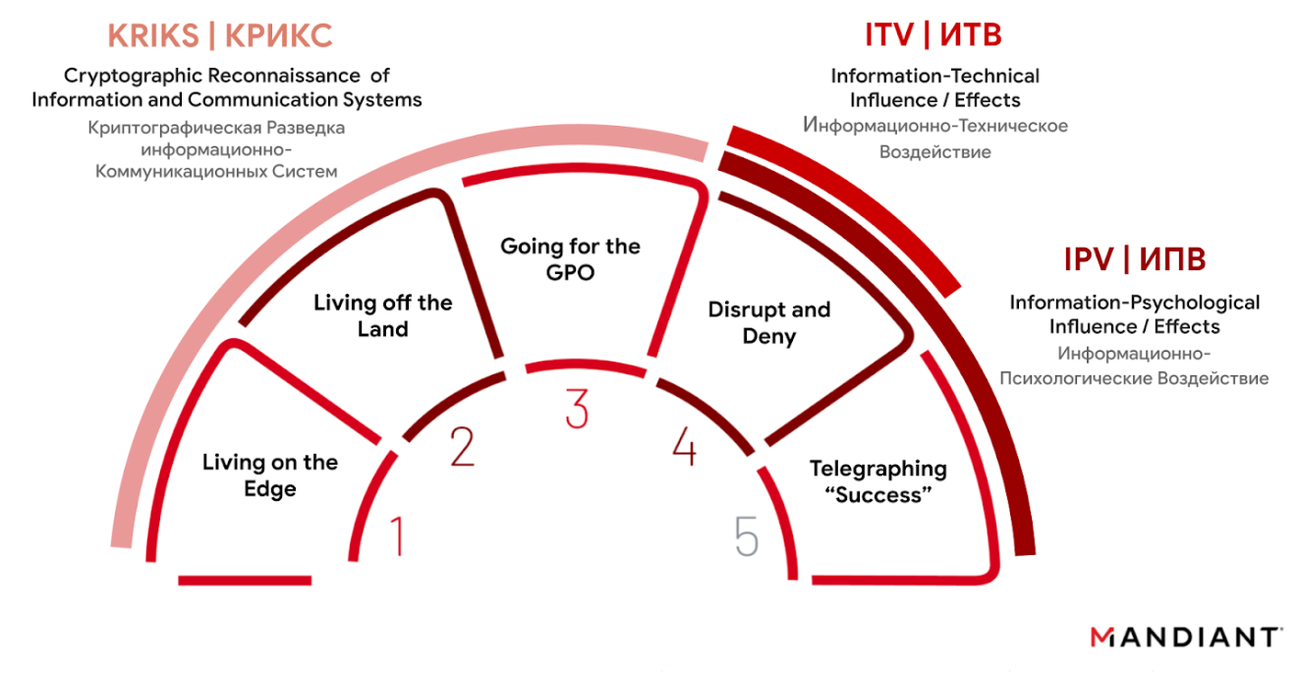

Figure 5: The GRU’s Disruptive Playbook
Russia’s approach to wiper operations in Ukraine highlights the importance of understanding threats from an adversary's perspective. By understanding the doctrine and cyber strategy of state threats, we can better understand how they might seek to target election-related processes.
Diversity of Threat Actors: More Players in the Game
Elections attract cyber threat activity from nearly every variety of threat actor that Mandiant tracks in terms of motivation, capability and intent. Mandiant assesses with high confidence that state-sponsored cyber threat actors pose the most serious risk to elections, particularly when these operations can combine state level resourcing with traditional cyber intrusion activity, disruptive and destructive capabilities, and information operations and hacktivist style tactics, elements of public-facing advertisement and amplification of threat activity claims.
-
State-sponsored actors: Government organizations, contractors, and others working on behalf of governments are the most persistent threat to elections. Military and security services are regularly tasked with cyber espionage intelligence collection against election related targets, with information operations and election interference increasingly becoming standard practice. State media services also have a role in information operations. Operations by these actors often benefit from long planning cycles, significant resources, and specific expertise. Based on previously observed activity taking place in the runup to elections, these operations are conducted for a variety of purposes, although rarely in an attempt to directly impact the process of voting and the tabulation of results.
-
Cybercrime: Financially motivated actors may affect elections despite no specific interest in the elections themselves. Ransomware and extortion operations target victims simply for their ability to pay. It is common for cyber criminals to offer compromised data or access for sale on underground forums, including from election-related organizations. The plentitude of election related organizations and systems significantly increases the likelihood of a related criminal event.
-
Hacktivists: Ideologically or politically motivated independent actors have carried out attacks on election related targets on several occasions. This activity is often sporadic, linked to foreign conflicts or domestic controversies, and typically causes only superficial impacts, such as the temporary disruption of election related websites.
-
Insider threats: Insider threats have become a concern for election officials given the privileged access they hold. Some are malicious insiders such as employees looking to steal data or sabotage the organization. Others are unintentional insiders such as employees who make mistakes or fall victim to phishing attacks.
-
Information operations as-a-service: Mandiant and open sources have documented PR firms using deceptive information operations tactics during elections to promote messaging that supports or criticizes candidates or issues. These tactics include coordinated inauthentic social media advocacy, comment brigading, and operating sock puppet accounts. Mandiant tracks several prominent examples, such as the HaiEnergy and Doppelganger campaigns, that we suspect or have confirmed conduct this activity on behalf of nation states.
HaiEnergy Exploits U.S. News Outlets via Newswire Services and Stage In-Person Protests
Mandiant believes the pro-People's Republic of China (PRC) HaiEnergy IO campaign is linked to Shanghai Haixun Technology Co., Ltd (上海海讯社科技有限公司), a Chinese PR firm. HaiEnergy used two self-described “press release” services—"Times Newswire" and "World Newswire" —and dozens of subdomains of legitimate U.S.-based news outlets to disseminate campaign materials that appear to come from trustworthy sources. The content is then further amplified by additional inauthentic news sites and associated social media accounts. Mandiant assessed the news sites to be inauthentic because although they presented themselves to be independent news organizations operating in a variety of countries and languages, they were all hosted on infrastructure owned by Haixun, they used the same Chinese-language HTML template, and they frequently included links to, or republished identical content from, other websites in the network.
Promoted articles praise the PRC and criticize U.S. foreign policy, politicians, and highlight domestic issues, such as ethnic tension or gender inequality. Mandiant observed HaiEnergy promote articles critical of Taiwanese President Lai Ching-te (candidate at the time of this observed activity), describing him as lacking political acumen and the Democratic Progressive Party (DPP) as plagued by internal conflicts and a series of scandals. HaiEnergy assets also promoted narratives positively portraying electoral changes implemented by the PRC in Hong Kong ahead of the district council election.
Significantly, Mandiant uncovered evidence that HaiEnergy financed at least two small, staged in-person protests in Washington, D.C., a marked escalation in tactics leveraged by pro-PRC actors. Both protests, which occurred around June and September 2022, were documented via video and subsequently used as source material to support narratives published by HaiEnergy assets and infrastructure (Figure 6).
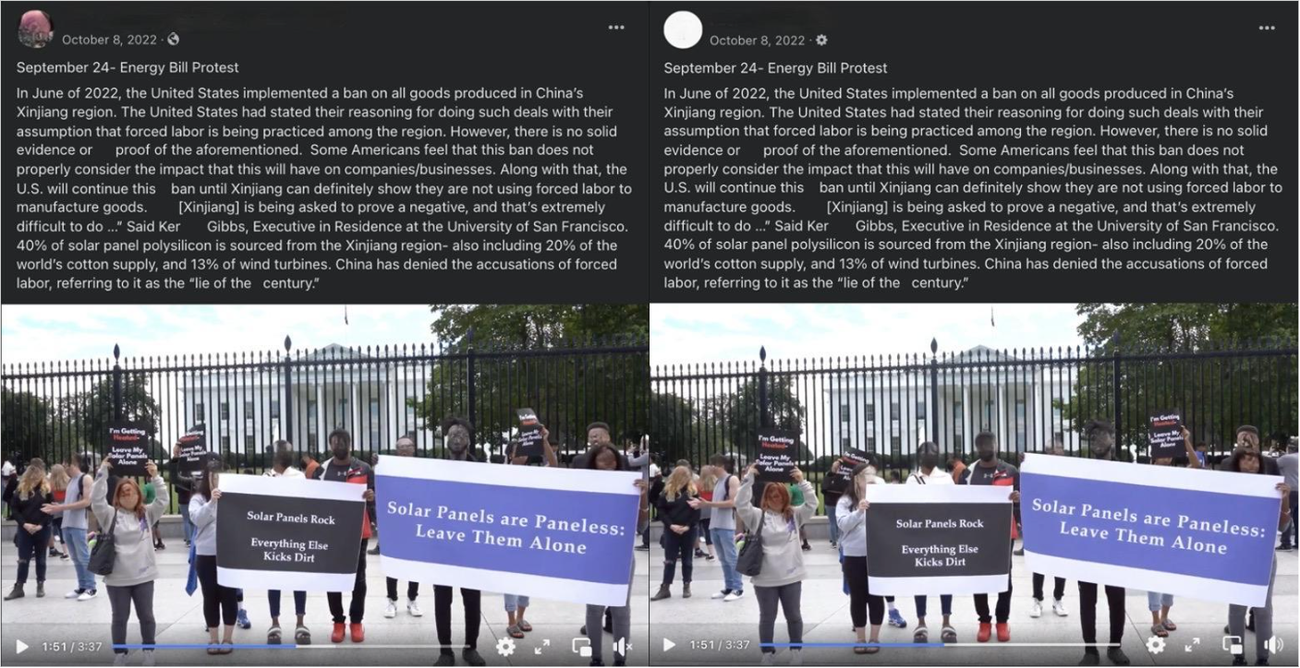

Figure 6: HaiEnergy Accounts Promote Identical Text from Times Newswire Article and Video of Protest in Washington, D.C.
State-Aligned Activity
State-sponsored cyber threat actors target election-related infrastructure for a variety of reasons, although rarely in an attempt to directly impact the result of an election or disrupt voting. Direct interference in elections comes with significant risk of retaliation and escalation leading to most states constraining their activity. Activity against election-related targets is therefore often intended to achieve other objectives, including:
-
Apply pressure on another government around a specific issue or as an attempt to influence foreign policy outcomes.
-
Retaliation for previous disputes between the two countries.
-
Amplify issues and causes in a foreign country that coincide with a government’s own national interests.
Mandiant compiled a list of state-aligned cyber threat actors and personas we assess to be likely to target election-related organizations in 2024 (Figure 7). In addition to threat actors focused on intrusion activity, we have also included groups that are involved in cyber threat activity targeting broad public audiences, such as hack and leak and information operations. This is because these public-facing campaigns often serve complementary objectives to more covert intrusion activity, and in some cases are coordinated.
To assess the likelihood of activity, Mandiant considered how likely different threat actors are to target election-related entities and the sort of activity they conduct. This list is based on groups that have been observed targeting government, civil society, media, or technology organizations.
This list should not be viewed as comprehensive; it is possible that additional known actors or previously unobserved groups will also engage in cyber threat activity related to 2024 elections. However, it could represent a useful guide for prioritizing defensive strategies and hunt missions.
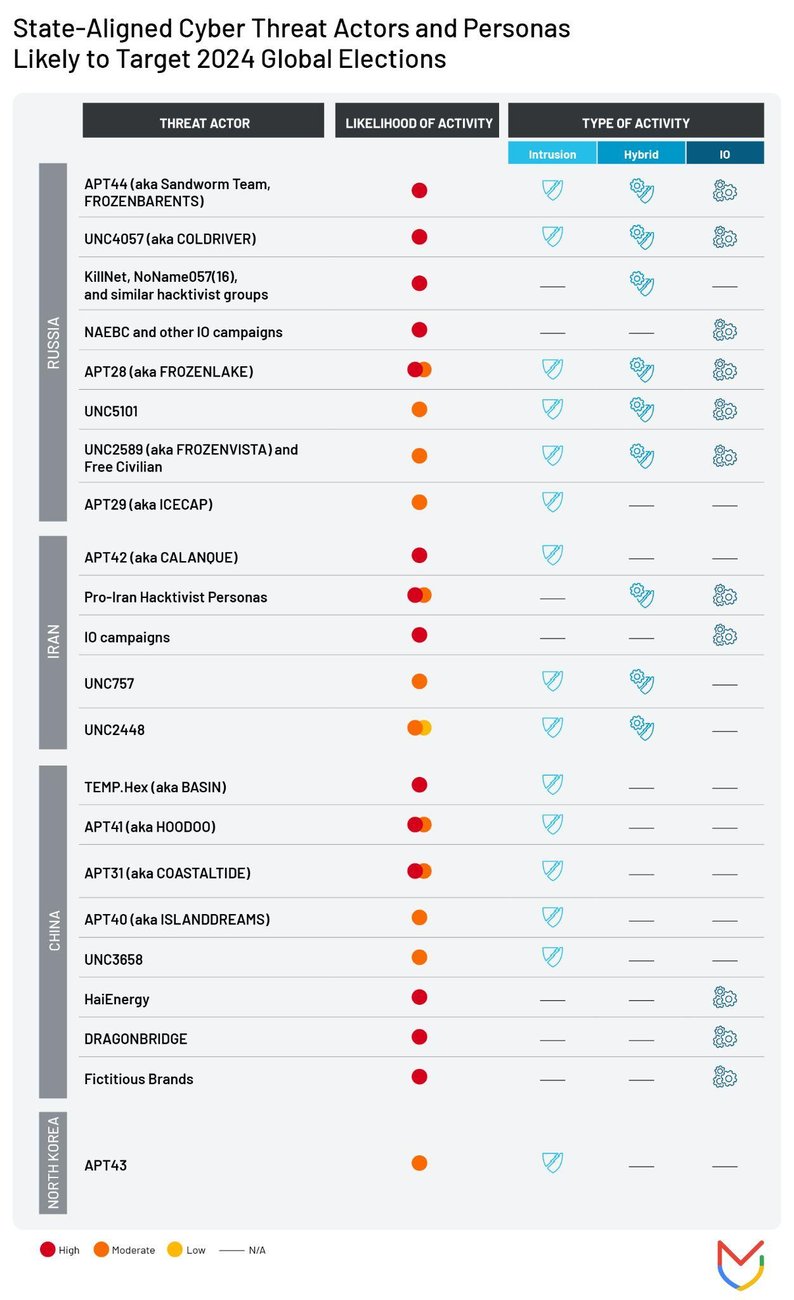

Figure 7: Relevant actors for 2024 global elections threat modeling
Russia
Mandiant assesses with high confidence that Russian state-sponsored cyber threat activity poses the greatest risk to elections in regions that Russia closely monitors, such as the U.S., the UK, and the EU. Multiple Russian groups have targeted past elections in the U.S., France, and Ukraine, and these groups have continued to demonstrate the capability and intent to target elections both directly and indirectly. However, we do not know how Russia’s operational tempo in Ukraine will impact any decision and resources available to target elections in 2024.


Figure 8: UNC4057 leak website attempting to inflame public debate around Brexit
Iran
Mandiant assesses with moderate confidence that the risk of Iranian cyber espionage and cyber-enabled influence campaigns will rise as elections approach in key nations of interest to the Islamic Republic, such as counterparts in the currently stalled nuclear negotiations, and countries offering support to Israel during current fighting in Gaza. Past Iranian activity targeting elections has primarily focused on the U.S., and has involved intrusion activity as well as online narrative promotion, claimed data leaks, and attempted voter intimidation. However, observations suggest that Iranian cyber threat groups are currently focused on domestic surveillance, the Gaza conflict, and Iranian opposition organization People's Mojahedin of Iran (MEK), potentially reducing the likelihood of large-scale attempts to interfere with global elections in 2024.
China
Mandiant expects PRC state-sponsored intrusions to focus on election-related targets for intelligence collection while pro-PRC influence operations generally praise China and undermine its adversaries. Mandiant has seen pro-China information operations campaigns carry out election-related activity in the U.S., Taiwan, and Hong Kong. These campaigns used AI-generated imagery and video content, and used increasingly nuanced tactics, such as posing as legitimate organizations or real individuals, to target and engage authentic users with some success. A segment of their activity appears to have increased audience engagement in the form of comments, likes, and/or shares from seemingly authentic accounts. As of the time of writing, Mandiant has not observed Chinese state-sponsored actors combine intrusion activity with information operations, though we have observed pro-PRC actors using falsified allegedly leaked materials to drive campaigns.
Observed Activity Surrounding the January 2024 Taiwanese Election
- Cyber Espionage: Mandiant observed TEMP.Hex and other PRC cyber espionage actors target Taiwanese organizations in the education, technology, government, and telecommunications sectors in the weeks leading up to and following Taiwan’s January 2024 election. In late summer, TAG tracked multiple PRC APT phishing campaigns targeting members of all three political parties, the TPP, the DPP, and the KMT. More broadly, TAG noted a substantial increase in Chinese cyber espionage targeting of Taiwan in 2023 compared to 2022.
- Information Operations: In the days surrounding the 2024 Taiwan presidential election held on Jan. 13, 2024, Mandiant observed an influx of pro-PRC information operations (IO) activity promoting a wide variety of narratives pertaining to the election. Mandiant identified three notable operations that leveraged seeded content and/or purportedly leaked information to promote narratives containing ad hominem attacks against outgoing President Tsai Ing-wen and President-elect Lai Ching-te. Allegedly leaked materials included a dubious DNA report purportedly providing evidence supporting the narrative that Lai has an illegitimate child and documents and audio recordings cited in a video as purported evidence supporting the claim that Lai had worked as a government informant, spying on DPP officials. We have not independently validated the authenticity of the allegedly leaked information; however, multiple sources, including official statements and credible media reports, indicate that the various alleged "leaked" information is likely false.
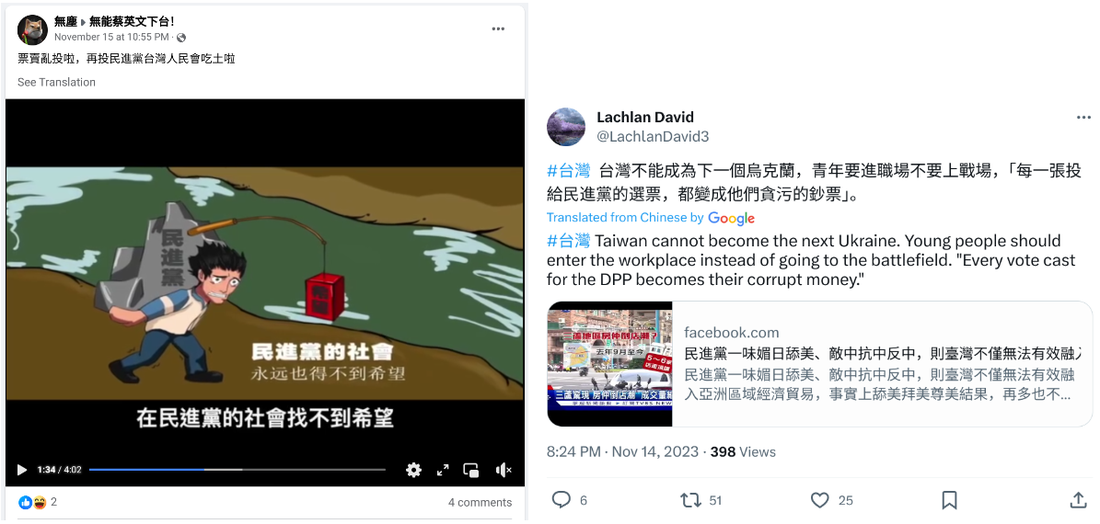

Figure 9: Sample Posts by DRAGONBRIDGE Accounts Targeting the 2024 Taiwan Presidential Election with Chinese-Language Posts Attempting to Discourage Taiwanese Citizens from Voting for the DPP
North Korea
Prior to the April 10, 2024 election, Mandiant forecast that Democratic People’s Republic of Korea (DPRK) government-affiliated actors would conduct campaigns to collect relevant intelligence from South Korean government organizations, political parties, and technology and manufacturing firms around the 2024 South Korean legislative election. In early 2024, Mandiant tracked operations associated with several North Korean threat groups targeting South Korean civil society and nonprofits, media entities, and other organizations.
Conclusion
Impacts to elections are not a foregone conclusion. Many of the aforementioned actors have struggled to influence or achieve significant effects, despite their best efforts. Wary and experienced defenders and populations are harder targets and without the element of surprise adversaries will be at a disadvantage.
Within Google, we are blending different perspectives on the threat landscape across TAG, Mandiant, VirusTotal, Google Cloud, and Trust & Safety. And we’re sharing information about intelligence, insights, and the action we’re taking with the security community and broader public through a variety of fora, such as our Google Safety Engineering Centers, Mandiant reporting, and the quarterly TAG Bulletin on the coordinated influence operation campaigns that Google disrupts.
Additional tools and resources
For mitigation and hardening recommendations, please review the following:
-
How to Understand and Action Mandiant's Intelligence on Information Operations blog post
-
Proactive Preparation and Hardening to Protect Against Destructive Attacks white paper
-
Linux Endpoint Hardening to Protect Against Malware and Destructive Attacks white paper
-
Distributed Denial of Service (DDoS) Protection Recommendations white paper
Google offers a suite of free of cost tools to help protect high-risk users from the most pervasive digital attacks, to which politicians, journalists, and campaigns are often most vulnerable. Examples include protecting accounts from targeted attacks with Advanced Protection Program and safeguarding campaign websites from DDoS attacks with Project Shield. Review these linked blog posts for more specifics on how Google is supporting the U.S., Indian, and EU elections this year.

