Make Google part of your security team anywhere you operate, with defenses supercharged by AI

Sunil Potti
VP/GM, Google Cloud Security
Protecting people, data, and critical assets is a crucial responsibility for modern organizations, yet conventional security approaches often struggle to address the escalating velocity, breadth, and intricacy of modern cyberattacks. Bolting on more new security products is simply not a viable long-term strategy.
What organizations need from their security solutions is a convergence of essential capabilities that brings simplicity, streamlines operations, and enhances efficiency and effectiveness.
Today at Google Cloud Next, we are announcing innovations across our security portfolio that are designed to deliver stronger security outcomes and enable every organization to make Google a part of their security team.
Increasing speed and productivity with Gemini in Security
Generative AI offers tremendous potential to tip the balance in favor of defenders and we continue to infuse AI-driven capabilities into our products. Today we’re announcing the following new AI capabilities:
Gemini in Security Operations is coming to the entire investigation lifecycle, building on our December GA of natural language search and case summaries in Chronicle. A new assisted investigation feature, generally available at the end of this month, will guide analysts through their workflow wherever they are in Chronicle Enterprise and Chronicle Enterprise Plus. Gemini recommends actions based on the context of an investigation, and can run searches and create detection rules to improve response times.
Plus, analysts can now ask Gemini for the latest threat intelligence from Mandiant directly in-line — including any indicators of compromise found in their environment — and Gemini will navigate users to the most relevant pages in the integrated platform for deeper investigation.
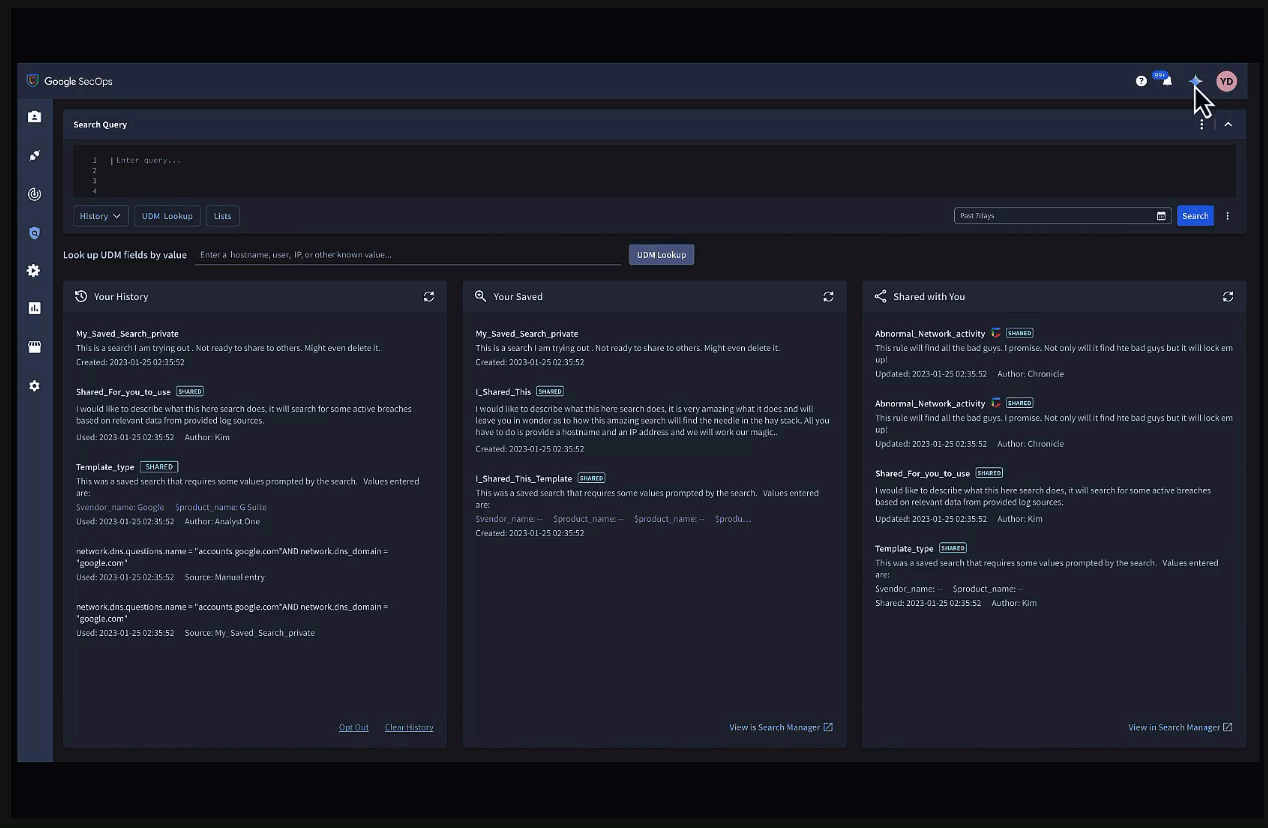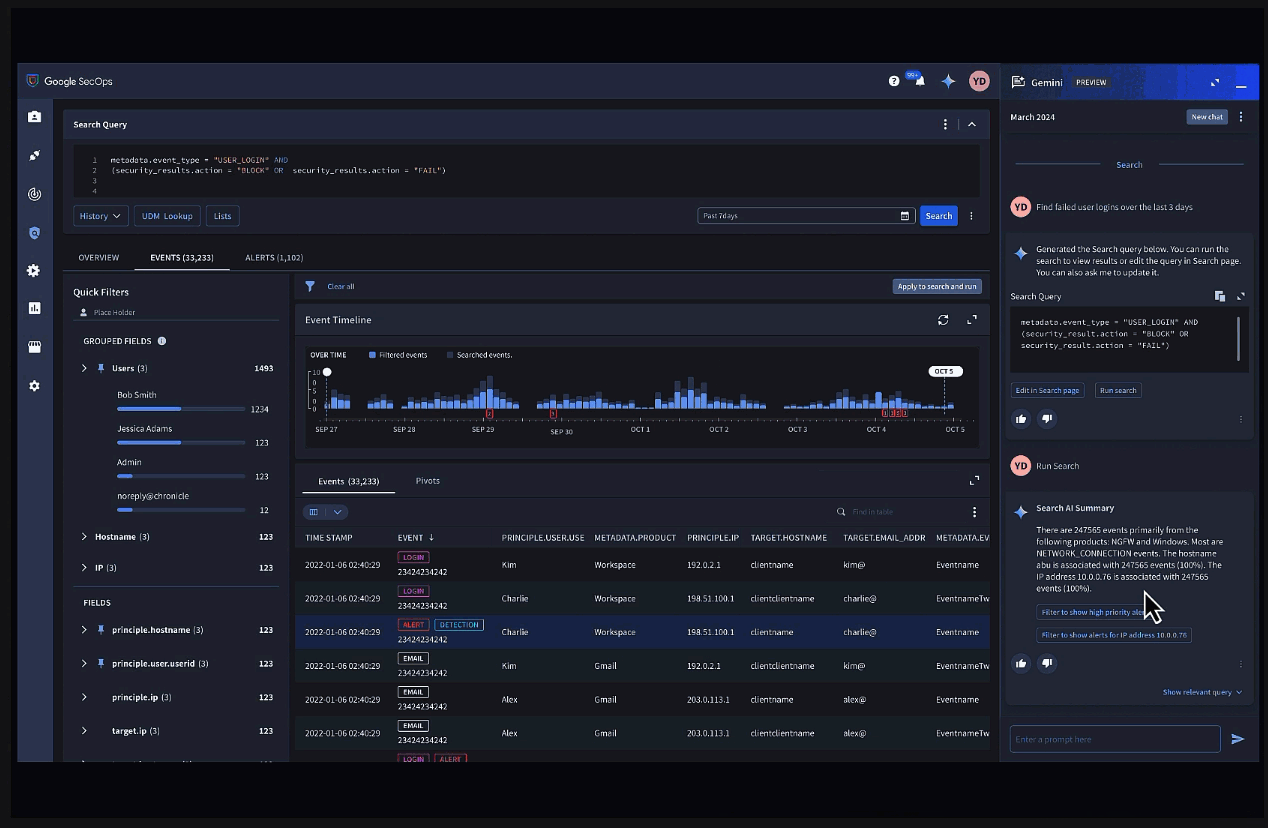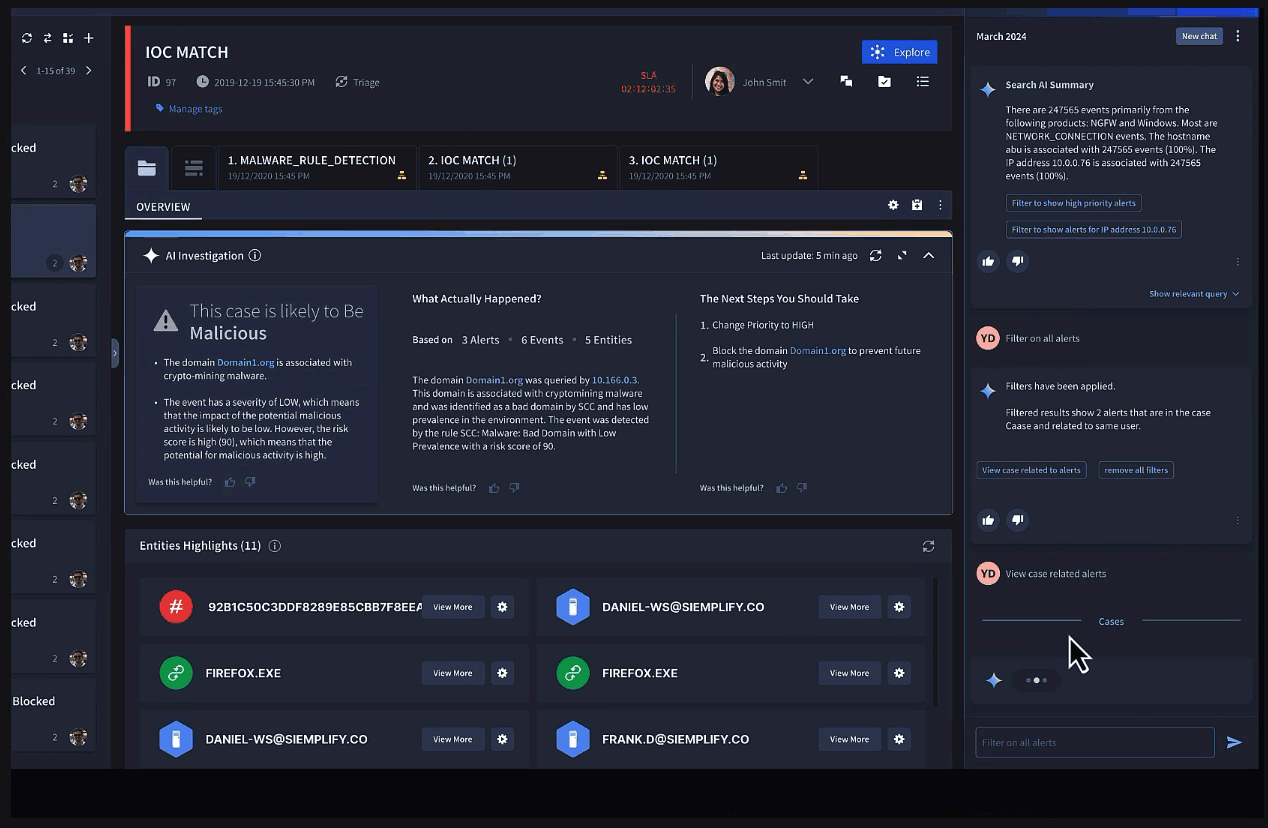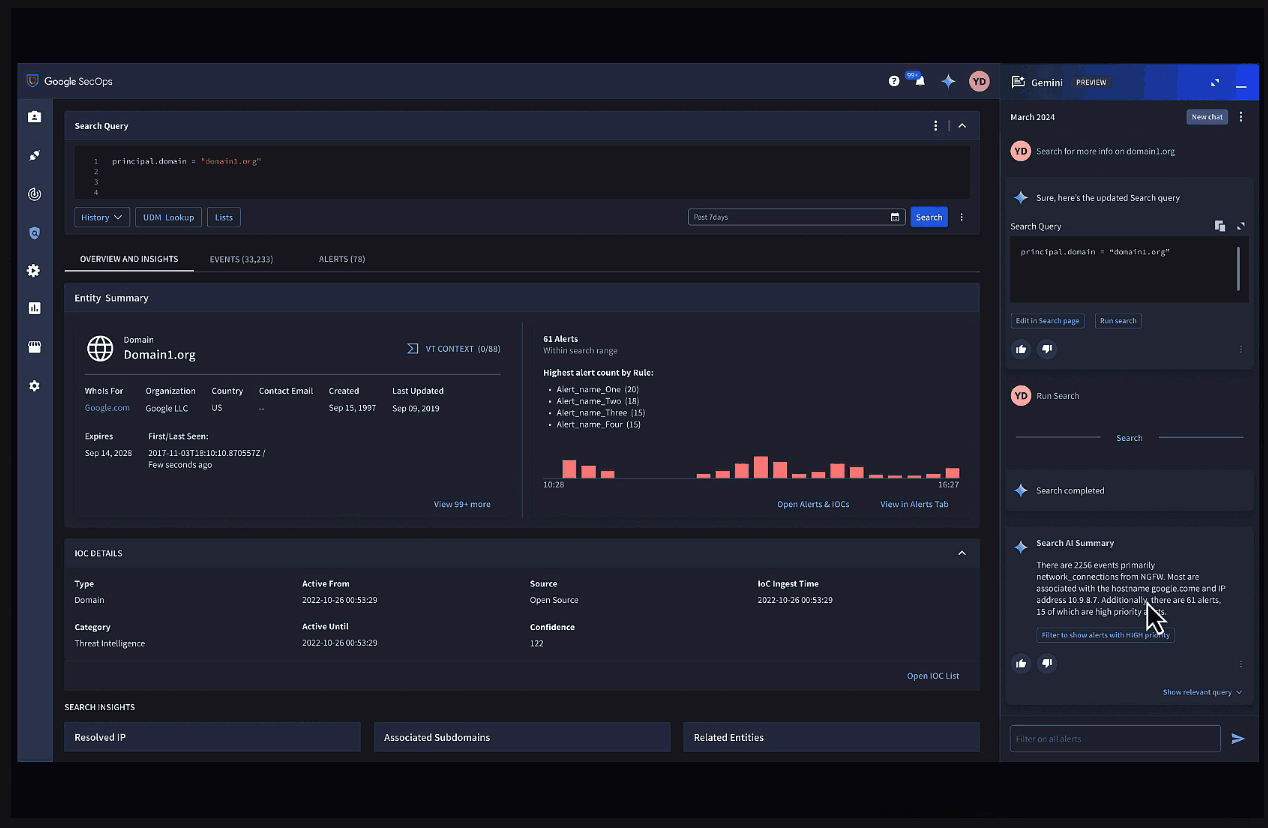

Gemini in Security Operations allows users to quickly investigate incidents and alerts using conversational chat in Chronicle.
“Gemini in Security Operations is enabling us to enhance the efficiency of our Cybersecurity Operations Center program as we continue to drive operational excellence,” said Ronald Smalley, senior vice president of Cybersecurity Operations, Fiserv. “Detection engineers can create detections and playbooks with less effort, and security analysts can find answers quickly with intelligent summarization and natural language search. This is critical as SOC teams continue to manage increasing data volumes and need to detect, validate, and respond to events faster.“
Gemini in Threat Intelligence now offers conversational search across Mandiant’s vast and growing repository of threat intelligence directly from frontline investigations — a grounded experience, now in preview. Plus, VirusTotal now automatically ingests OSINT reports, which Gemini summarizes directly in the platform — a feature that’s generally available now.
Gemini in Security Command Center now offers preview features that let security teams search for threats and other security events using natural language. It can also provide summaries of critical- and high-priority misconfiguration and vulnerability alerts, and summarize attack paths to help understand cloud risks for remediation.
We are also infusing AI in many of our cloud platform’s security services. Today, we’re announcing previews of new capabilities in Gemini Cloud Assist, including:
-
IAM Recommendations, which can provide straightforward, contextual recommendations to remove roles from over-permissioned users or service accounts to help uplevel IAM posture and reduce risk exposure.
-
Key Insights, which can provide assistance during encryption key creation based on its understanding of your data, your encryption preferences, and your compliance needs.
-
Confidential Computing Insights, which can recommend options for adding confidential computing protection for your most sensitive workloads based on your data and your compute usage.
Delivering a new frontline of defense for the enterprise
Chrome Enterprise Premium is a new offering that redefines, simplifies, and strengthens endpoint security. It brings together the most popular and trusted enterprise browser with Google’s advanced security capabilities, including threat and data protection, Zero Trust access controls, enterprise policy controls, and security insights and reporting.
With Chrome Enterprise Premium, which is generally available today, hundreds of millions of enterprise users can get additional protection delivered instantly where they do their work every day.


"With Chrome Enterprise Premium, we have confidence in Google’s security expertise, including Project Zero’s cutting-edge security research and fast security patches. We set up data loss prevention restrictions and warnings for sharing sensitive information in applications like Generative AI platforms and noticed a noteworthy 50% reduction in content transfers,” said Nick Reva, head of corporate security engineering, Snap Inc.
Turning intelligence into action
Our focus on intelligence-driven outcomes continues with the launch of Applied Threat Intelligence in Google Security Operations. Applied threat intelligence takes our industry-leading global threat visibility and automatically applies it to each customer’s unique environment. It can help security operations teams uncover more threats with less effort and use the most up-to-date threat intelligence to address them before they create damage or loss.
Managing cloud risk
Security Command Center Enterprise, the industry’s first cloud risk-management solution that fuses proactive cloud security and enterprise security operations, is now generally available. This new solution offers security teams a single view of their posture controls, active threats, cloud identities, data, and more, while integrating remediation and issue accountability into end-to-end workflows.
Mandiant Hunt for Security Command Center Enterprise is now in preview, and offers on-demand human expertise that can become an extension of internal security operations teams. Hundreds of elite-level analysts and researchers are available on-call to proactively find elusive threats in organizations’ SCC environments.
New security capabilities in our trusted cloud
We continue our regular delivery of new security controls and capabilities on our cloud platform to help organizations meet evolving policy, compliance, and business objectives. Today we’re announcing the following updates:
For Identity and Access Management:
-
Privileged Access Manager (PAM), now available in preview, is designed to help mitigate risks tied to privileged access misuse or abuse. PAM can help customers shift from always-on standing privileges towards on-demand access with just-in-time, time-bound, and approval-based access elevations.
-
Principal Access Boundary (PAB) is a new, identity-centric control now in preview. It can empower security administrators to enforce restrictions on IAM principals so that they can only access authorized resources within a specific defined boundary.
For Network Security:
-
Cloud NGFW Enterprise is now generally available. Our cloud-first next generation firewall (NGFW) includes threat protection powered by Palo Alto Networks with a unique distributed architecture that can provide granular control at the workload level.
-
Cloud Armor Enterprise, now generally available, offers a pay-as-you-go model that includes advanced network DDoS protection, web application firewall capabilities, network edge policy, adaptive protection, and threat intelligence to help protect your cloud applications and services.
For Data Security:
-
Confidential Accelerators: Confidential VMs on Intel TDX are now in preview and available on the C3 machine series with Intel TDX. For AI and ML workloads, we support Intel AMX, which provides CPU-based acceleration by default on C3 series Confidential VMs. In addition, Confidential Compute will also be coming to A3 VMs with NVIDIA H100 GPUs in preview later this year. With these announcements, our Confidential Computing portfolio now spans Intel, AMD, and NVIDIA hardware.
-
Sensitive Data Protection integration with Cloud SQL is now generally available, and is deeply integrated into the Security Command Center Enterprise risk engine. This powerful combination can pinpoint high-value assets, analyze vulnerabilities in databases, and simulate real-world attack scenarios that can enable you to proactively address risks and safeguard data.
-
Key management with Autokey is now in preview. Autokey simplifies creating and managing customer encryption keys (CMEK) by ensuring you use the right key type for each resource, thus reducing complexity and management overhead. Plus, Autokey can help you adhere to industry best practices for data security.
-
Expanded regions available for bare metal HSM deployments allows you to deploy your own HSMs in PCI-compliant facilities with your Google Cloud workloads.
For our Regulated Cloud offerings:
-
Regional Controls for Assured Workloads is now in preview and is available in 32 cloud regions in 14 countries. The Regional Controls package can enforce data residency for customer content at rest, offers administrative access transparency, as well as compliant service restriction and monitoring. Regional controls are available at no additional cost.
-
Audit Manager is now in preview. Audit Manager can help customers drastically simplify their compliance audit process by automating control verification with proof of compliance for their workloads and data on Google Cloud.
Take your next security steps with Google Cloud
Google’s decade of AI innovation, coupled with our security expertise, means we are strongly positioned to help you protect your users and brand by becoming an integral part of your security team.
For more on our Next ‘24 announcements, you can watch our security spotlight, and check out the many great security breakout sessions at Google Cloud Next — live or on-demand.